CA User Activity Reporting Module (CA UARM) is a log management solution where the management, collection and archiving log data across the IT environment is fully automated.
CA UARM as a core for many of the available products CA Technologies provides is a robust log management solution. Security administrator can access the data in a few clicks and present them in a clear manner and dig into the events occuring around the organization. Since the product itself is sold as a module to number of security solutions which as of today are ControlMinder, SiteMinder, IdentityMinder, GovernanceMinder, AuthenticationMinder and DataMinder the customer gets a hold on two solutions in one product. The scenario which often comes into play is splitting the governance among the security department employees with log management duties and the chosen 'minder' solution duties which supports effective administration of the ongoing operations in the end.
CA UARM can mitigate or completely remove possible audit findings which are a major counterpart when budgeting the security investments.
Users accessing servers or applications using legacy accounts. This often occurs when internal mobility for employees is preferred. A four-eye principle can be breached by self-authorizing actions which require a counterpart (such as transactions, approvals, etc.).
Investigation when a loss of sensitive data has occured or there is at least a suspicion of such event.
Investigation on possible wrongdoings within methodology steps.
To get a clearer picture on how UARM presents the data the list below shows a few sample reports. These reports are out-of-the-box and can be customized to customer's requirements or comfort. Our experience finds the premade reports quite clear however tweaking these reports or possibly creating a completely new is based either on infrastructure to watch or running software that might spread wide in the organization or simply on what policies the security administrator has to follow.
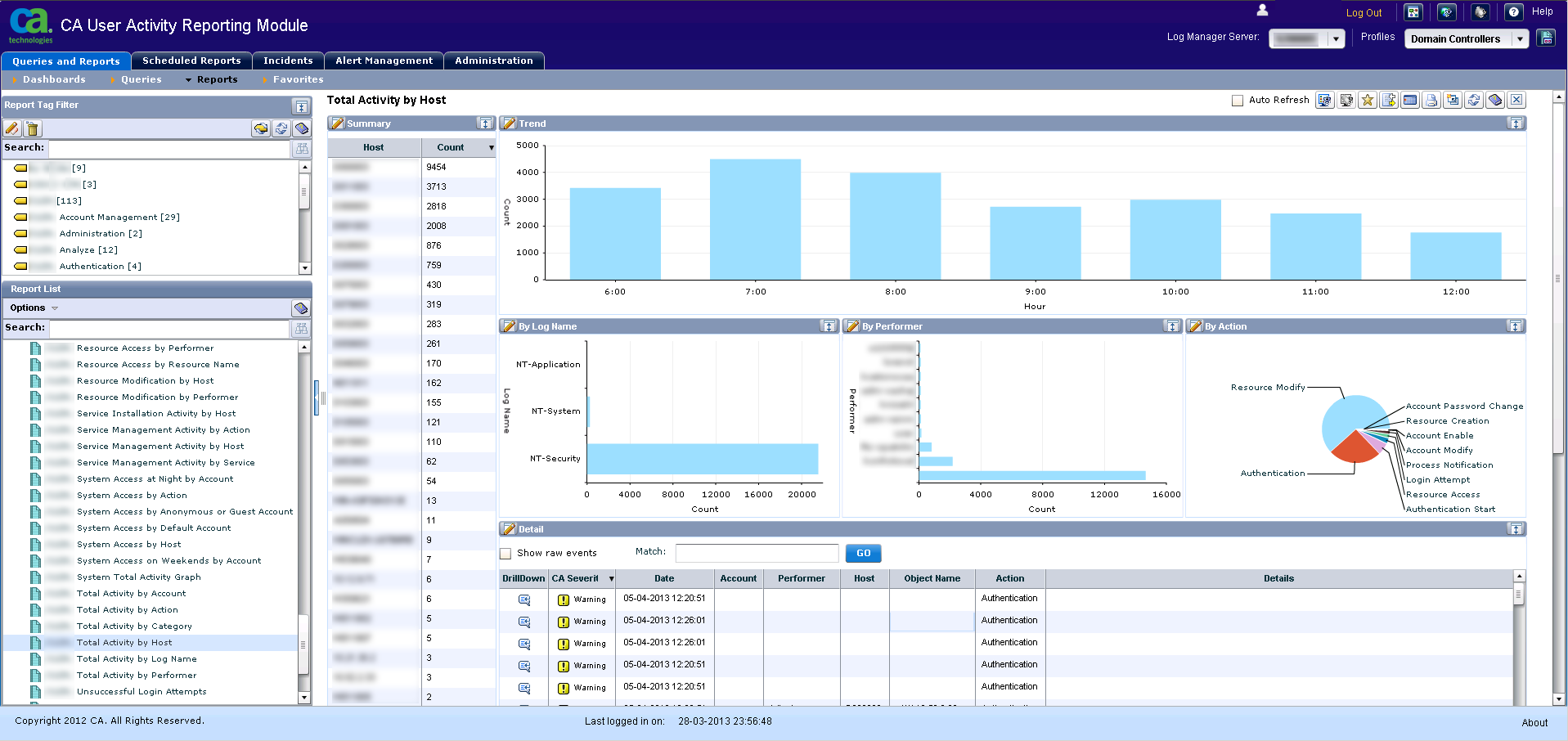
Total activity by host
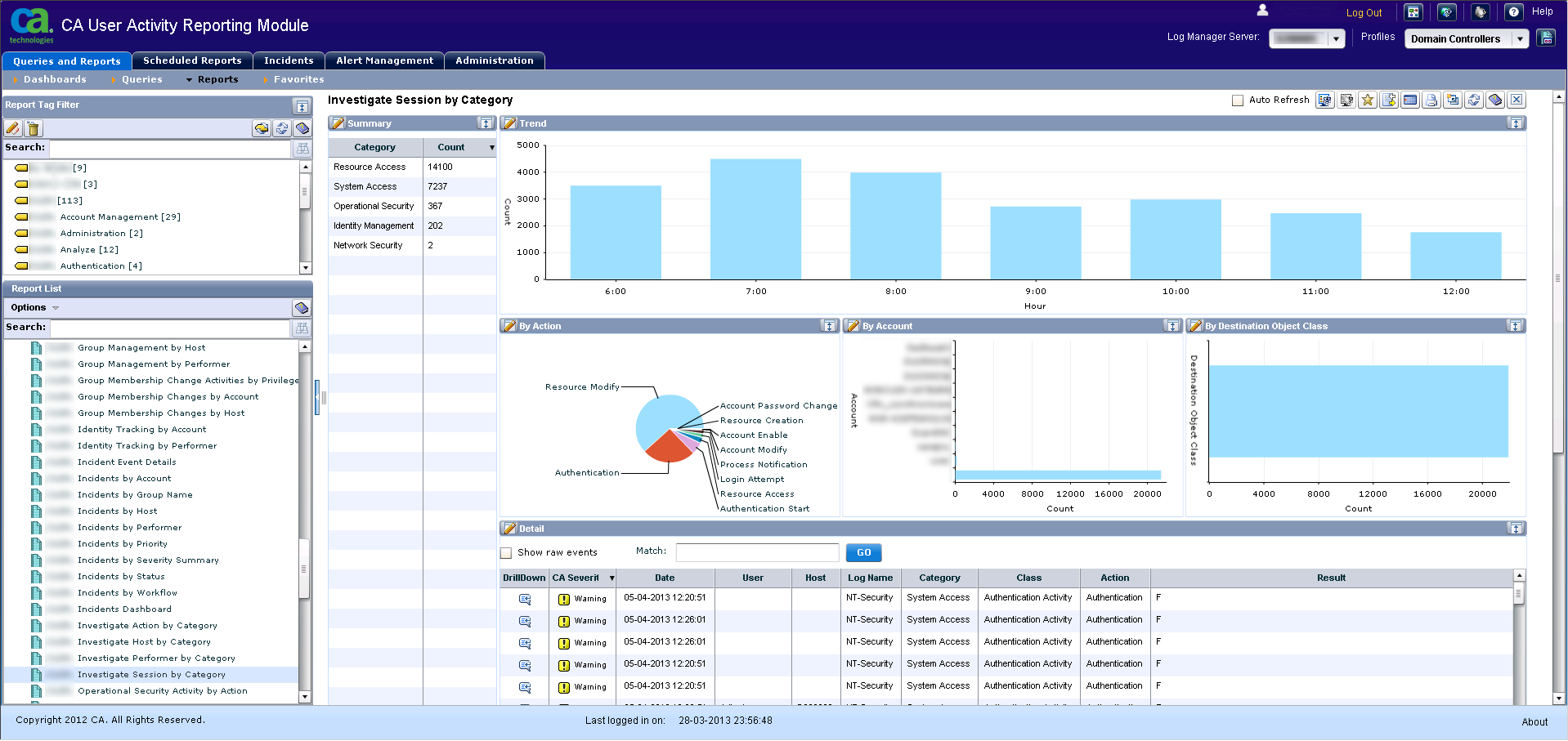
Investigate session by category
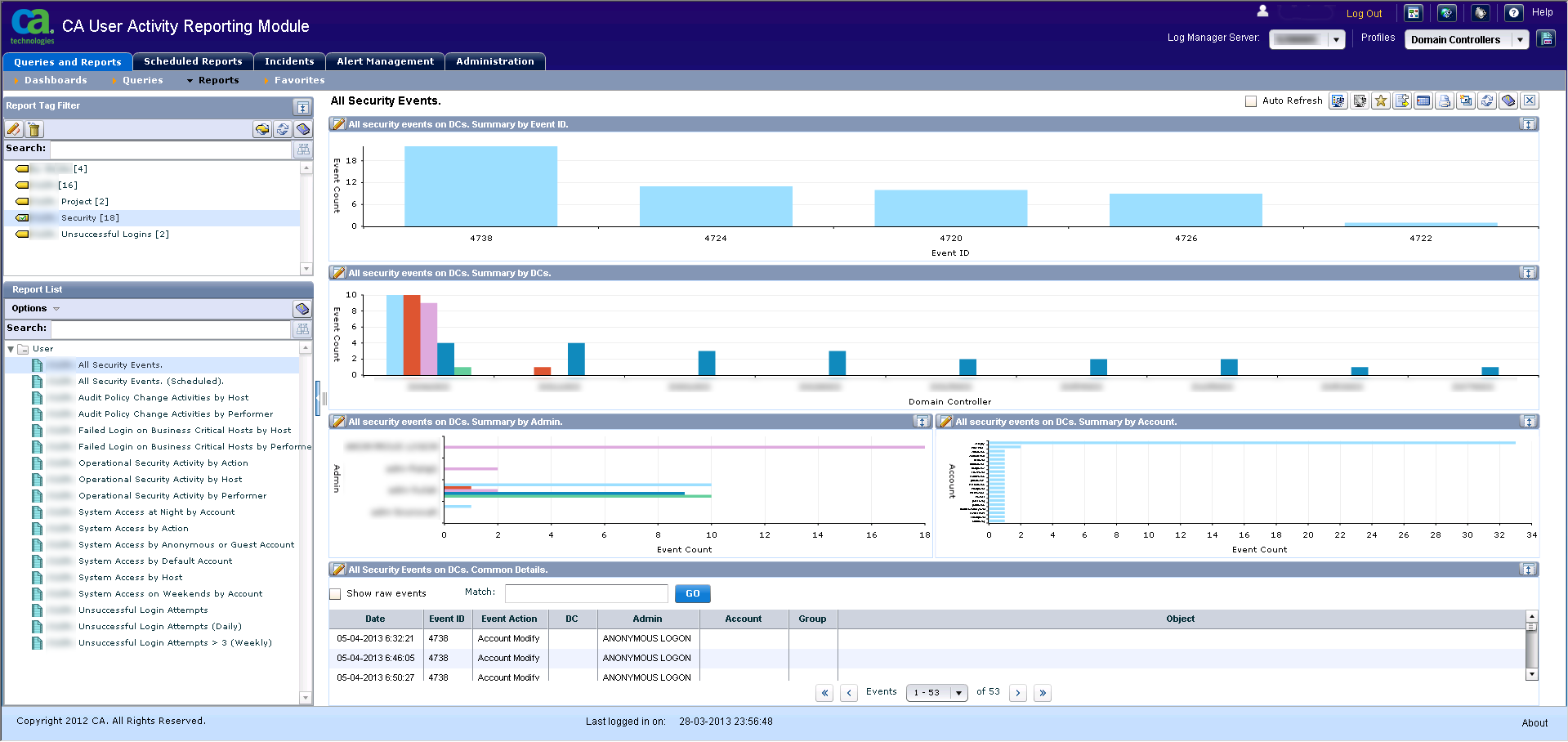
All security events
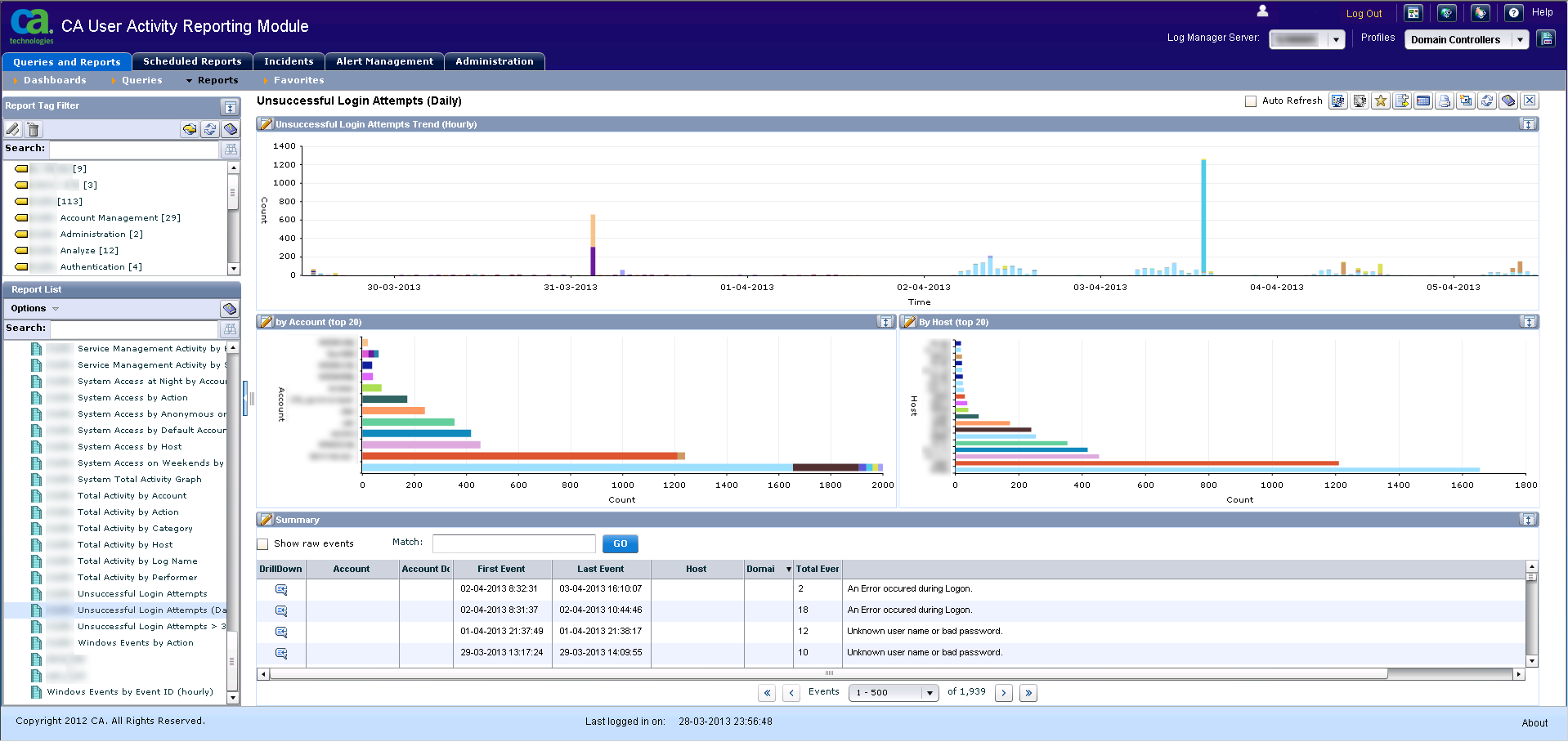
Unsuccessful login attempts
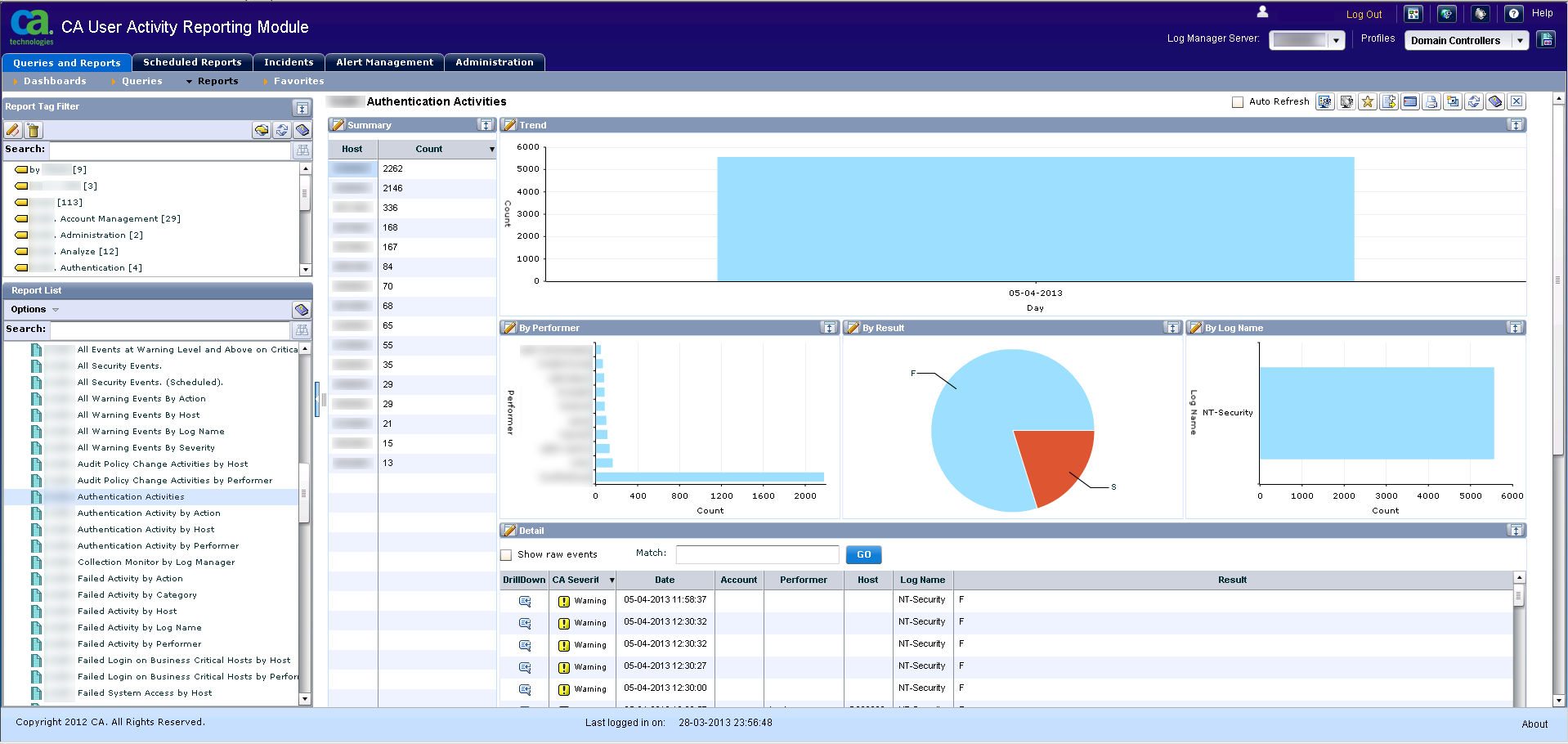
Authentication activities
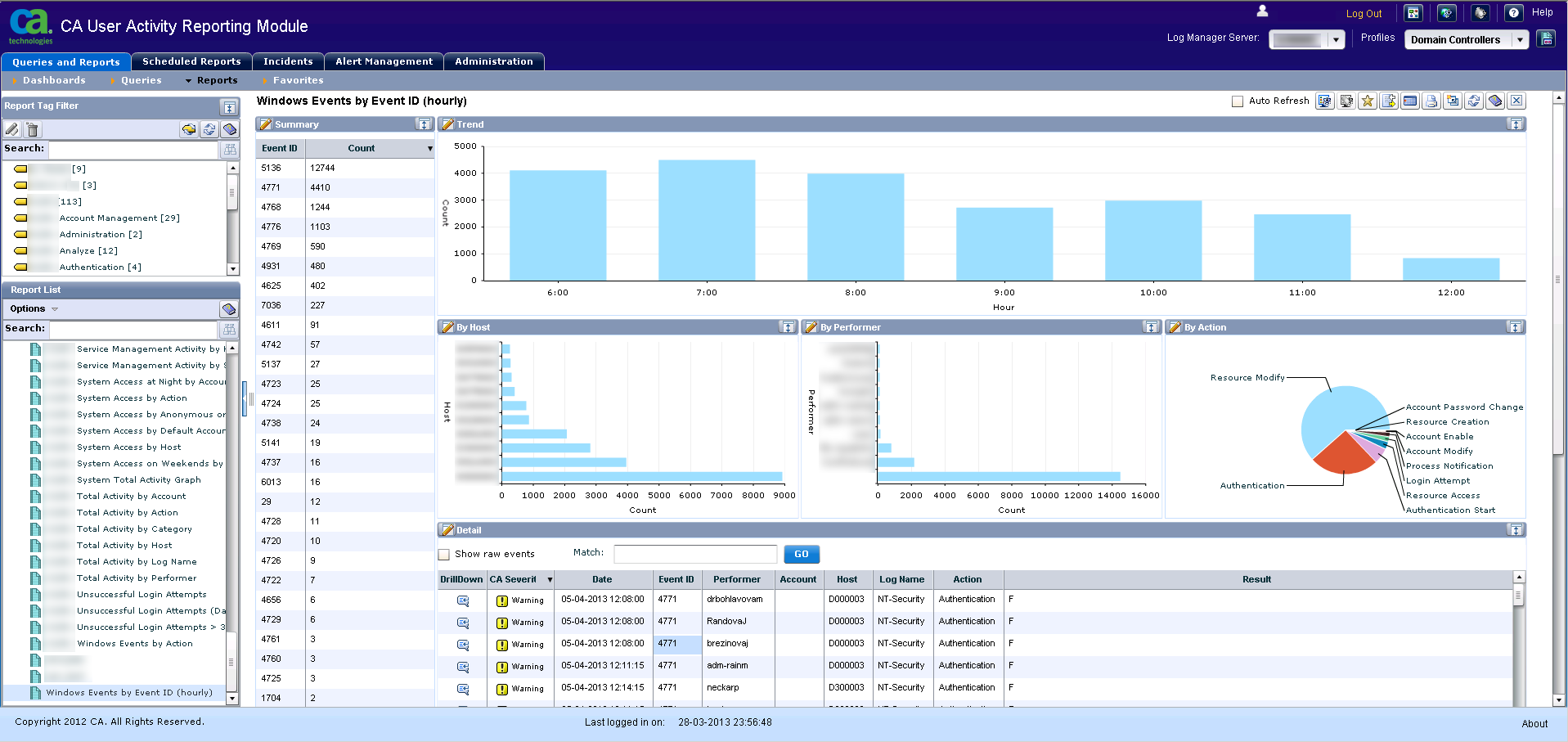
Windows Event by Event ID
We are ready to give recommendations on what to use out of the stack of more than a 100 premade reports available from CA Technologies. For special requests and cases we provide expertise to create customized reports required in your organization.